Nabz Software Suite Integrates Removal of the New TeslaCrypt Ransomware Virus
Cybercriminals have been really busy coining advanced iterations of ransomware hoaxes lately. One of the nasty out-turns of their crooked mindset is the TeslaCrypt virus that encrypts all victim’s files and substitutes their original extensions with .vvv format.
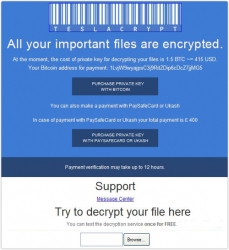
Los Angeles, CA, December 05, 2015 --(PR.com)-- Ransomware infection leads to inaccessibility of the user’s documents, personal photos, video files and other objects that aren’t system-related. TeslaCrypt, an extremely dangerous file-encrypting infection, is the one to blame for this messy scenario.
The newest version of so-called .vvv Trojan is capable of circumventing antivirus solutions when attacking systems, and in most cases the users have no clue the compromise is happening until a how_recover_file window pops up. It contains the essentials of data recovery options, providing links to the victim’s personal decrypt page and listing the conditions to be met for restoring the data. In particular, a ransom amounting to several Bitcoins is to be submitted to the criminals, which is the prerequisite of obtaining the private decryption key that’s stored on the remote Command and Control server. The infected person has limited time to pay up, and the sum will double if the deadline isn’t met.
The crypto standard used for encoding the victim’s sensitive information implies that a pair of keys is generated. One of them, the public key, is kept on the contaminated workstation, but it’s useless for troubleshooting unless the above-mentioned private key is at the user’s disposal. Security professionals have made brute-forcing attempts to circumvent the crypto, to no avail thus far.
Despite the fact that getting out of this quandary seems to be payment-related only, malware examiners have figured out that using Shadow Volume Copies and forensic solutions may do the recovery trick at least for some files. Certainly, keeping file backups in the cloud or on physical storage is the best way of avoiding the worst consequences. In the era of ubiquitous ransomware, this sort of practice should become every PC user’s priority.
Source: http://nabzsoftware.com/types-of-threats/vvv-file
The newest version of so-called .vvv Trojan is capable of circumventing antivirus solutions when attacking systems, and in most cases the users have no clue the compromise is happening until a how_recover_file window pops up. It contains the essentials of data recovery options, providing links to the victim’s personal decrypt page and listing the conditions to be met for restoring the data. In particular, a ransom amounting to several Bitcoins is to be submitted to the criminals, which is the prerequisite of obtaining the private decryption key that’s stored on the remote Command and Control server. The infected person has limited time to pay up, and the sum will double if the deadline isn’t met.
The crypto standard used for encoding the victim’s sensitive information implies that a pair of keys is generated. One of them, the public key, is kept on the contaminated workstation, but it’s useless for troubleshooting unless the above-mentioned private key is at the user’s disposal. Security professionals have made brute-forcing attempts to circumvent the crypto, to no avail thus far.
Despite the fact that getting out of this quandary seems to be payment-related only, malware examiners have figured out that using Shadow Volume Copies and forensic solutions may do the recovery trick at least for some files. Certainly, keeping file backups in the cloud or on physical storage is the best way of avoiding the worst consequences. In the era of ubiquitous ransomware, this sort of practice should become every PC user’s priority.
Source: http://nabzsoftware.com/types-of-threats/vvv-file
Contact
Nabz Software
James Voigt
844 326 2924
http://nabzsoftware.com
James Voigt
844 326 2924
http://nabzsoftware.com
Categories
